Link to challenge: https://academy.hacking-lab.com

Date Completed: 23 December 2019
Challenge
HV19.23 Internet Data Archive
|
1 2 3 4 5 |
Introduction Today's flag is available in the Internet Data Archive (IDA). Resources http://whale.hacking-lab.com:23023/ |
Solution
We are presented with the following website:
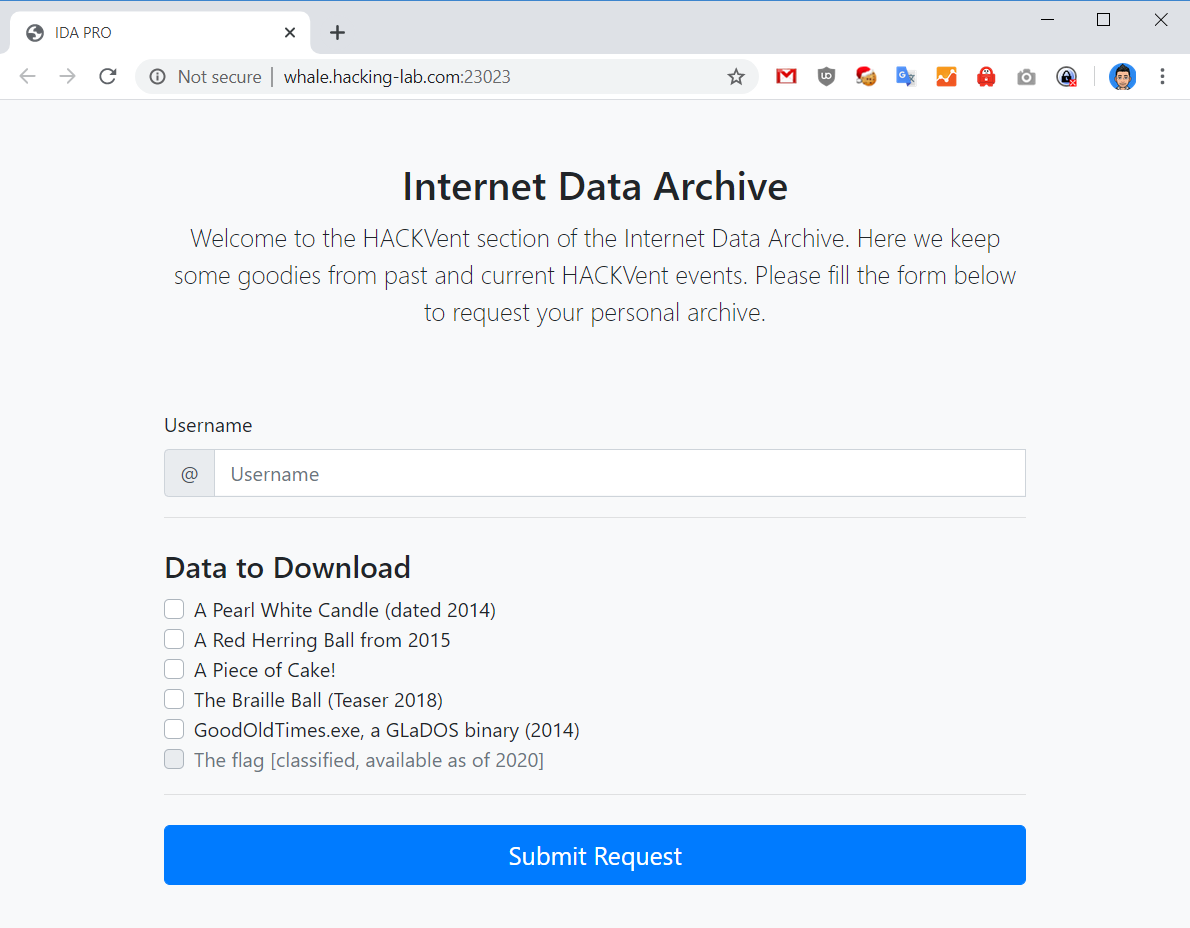
We are allowed to enter a username and select some data to download except the flag which is classified. Upon doing this a unique zip file is generated for us containing our files and we are also provided with a password that allows us to open the encrypted zip file.
By playing around with the website we learn the following things:
- Usernames are truncated to be at most 12 characters long (alphanumberis)
- Passwords are always 12 digits (alphanumeric) and look like this: BxxRGJAMpmbJ
- All links to download files contain the input username with -data appended. Example for username of mo: http://whale.hacking-lab.com:23023/tmp/mo-data.zip
- Can pass in req instead of req[] as PHP post argument to trigger PHP error:
123r /><b>Warning</b>: Invalid argument supplied for foreach() in <b>/var/www/html/archive.php</b> on line <b>19</b><br />No files! - Can pass in username[] instead of username as PHP post argument to make name be parsed as Array: http://whale.hacking-lab.com:23023/tmp/Array-data.zip
- We cannot use the username Santa (it is explicitly disallowed!)
We shortly find out that the tmp directory where files are hosted has indexing on and we can see all the files that are being created. By sorting by oldest files first we discover two interesting files:
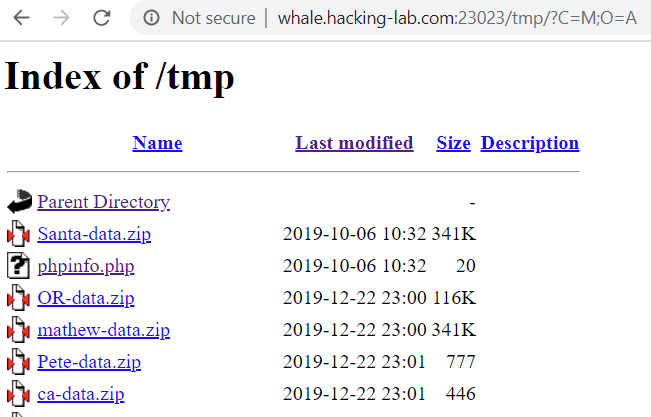
We download Santa-data.zip and discover that it contains a file called flag.txt! However, we do not know the password for this archive.
Assuming alphanumerics are used as the charset for the password our bruteforce complexity is 62^12 which not feasible.
Next, we inspect the phpinfo for any valuable information, we take note of the PHP version 7.4.1 and that the sodium module is loaded (although this doesn’t matter).
Next we write a password generator script to generate a lot of tokens:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
# Hackvent 2019 - Day 24 # Mo Beigi (https://mobeigi.com) import re import requests f = open("passwords.txt", "a") # Until user exits while True: r = requests.post('http://whale.hacking-lab.com:23023/archive.php', data={'username': 'Santa1', 'req[]': 'candle'}) if r.status_code == 200: m = re.search('<p>Your one-time Password is: <strong>(.*?)</strong></p>', r.text) if m: # Verify length token = m.group(1) if len(token) != 12: print(f'Unexpected token found: {token}') # Append to file f.write(token + "\n") f.flush() else: print('Failed to get token...trying again.') |
After generating 1000 passwords we run frequency analysis on the payload and discover that certain characters never appear. These characters are 0, 1, l, I, N, n, O, o. Perhaps these characters are committed as they look similar to other characters. Eliminating this characters from our charset brings down our bruteforce complexity to 54^12 which is still not feasible.
We note the title of the challenge page IDA Pro and after researching for IDA Pro PRNG we come across this interesting article:
https://devco.re/blog/2019/06/21/operation-crack-hacking-IDA-Pro-installer-PRNG-from-an-unusual-way-en/
The author describes the same exact charset that is in use here so we try to use the same approach to break the PRNG used to encrypt the Santa-data.zip file. We decide to use PHP for this with the same version 7.4.1 as the challenge website to ensure consistency.
We make the following bruteforce.php script:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
<?php # Hackvent 2019 - Day 24 # Mo Beigi (https://mobeigi.com) $alphabet = 'abcdefghijkmpqrstuvwxyzABCDEFGHJKLMPQRSTUVWXYZ23456789'; $alphaLength = strlen($alphabet) - 1; //put the length -1 in cache for ($i = 0; $i < pow(2,32)-1 ; $i++) { srand($i); $pass = ""; for ($j = 0; $j < 12; $j++) { $n = rand(0, $alphaLength); $pass .= $alphabet[$n]; } print($pass . "\n"); } ?> |
This script simply generates a random 12 length password using the first 12 bytes of randomness generated by the RNG for each seed between 0 to 2^32. However, we cannot save this data to disk easily so we will instead stream the data to a ZIP cracking utility like John the Ripper to attempt to crack the file on the fly.
We run:
|
1 2 3 |
zip2john Santa-data.hash > Santa.hash php bruteforce.php | john --stdin Santa.hash john --show Santa.hash |
After about 2 minutes we have a successful crack:
|
1 2 3 |
Santa-data.zip/flag.txt:Kwmq3Sqmc5sA:flag.txt:Santa-data.zip:Santa-data.zip 1 password hash cracked, 0 left |
Thus our password is Kwmq3Sqmc5sA and the original seed used was 4333287.
We open flag.txt to get our daily flag!
Flag: HV19{Cr4ckin_Passw0rdz_like_IDA_Pr0}